Zero Trust Framework: Trust No One, Verify Everything
In an ever-evolving threat landscape, where security breaches and data breaches seemingly dominate headlines, it has become apparent that traditional security approaches using VPN are no longer sufficient to protect organizations' critical assets. That's where the Zero Trust framework comes into play – revolutionizing security practices and mitigating risks in the modern era.
Before delving into the significance and impact of Zero Trust, let's briefly revisit the traditional security model. In the past, organizations primarily relied on the perimeter-based security model, widely known as the castle-and-moat approach. This approach focused on securing the network perimeter, assuming all users and devices within it were trustworthy. However, with the rise of sophisticated cyber threats, such as phishing attacks, social engineering, and insider threats, this model has proven inadequate
Introducing Zero Trust Framework:
To address modern security challenges, the Zero Trust framework was introduced. Rather than relying solely on network perimeters, Zero Trust operates on the principle of "never trust, always verify." It assumes that every user, device, and network request is potentially untrusted, regardless of its location – be it within or outside the organization's network.
Instead of granting unconditional access, Zero Trust enforces strict access controls, continuously verifying and validating the identity and security posture of all users and devices, regardless of their location or connection method. This framework ensures that access privileges are granted on a "need-to-know" and "least privilege" basis.
Key Principles:
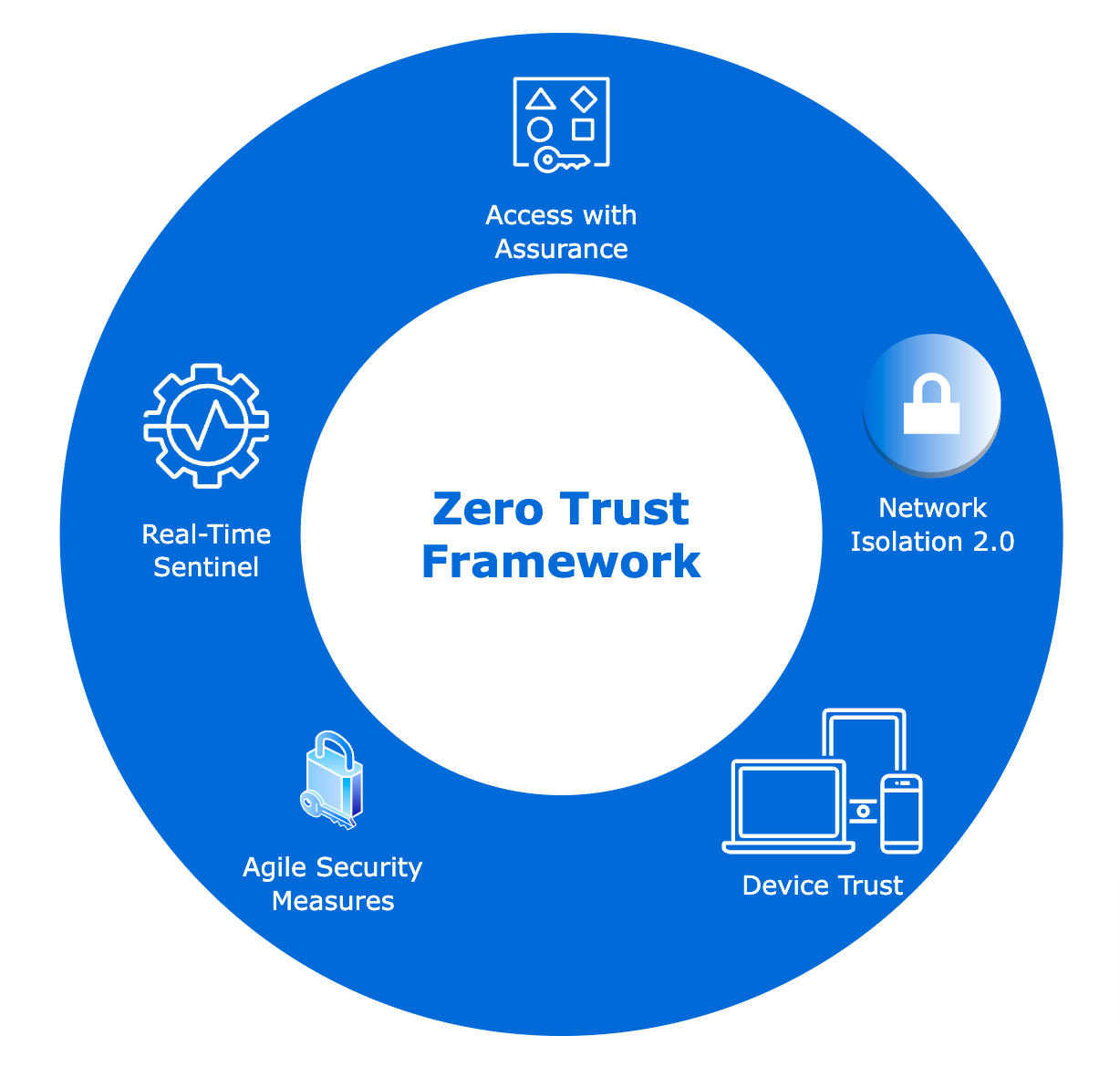
Zero Trust Framework has transformed Security. Here are the key principles:
Access with Assurance: With Zero Trust, security is no longer restricted to the network perimeter. Strict access controls are enforced based on factors such as user identity, device health, location, and context. Access is granted on a "need-to-know" basis. Users are continuously authenticated and authorized, regardless of their location, granting access only upon successful verification.
Network Isolation 2.0: Zero Trust promotes the implementation of micro-segmentation – dividing the network into small, isolated segments rather than a single, monolithic network. This helps contain breaches and restrict lateral movement within the network if one segment is compromised.
Device Trust Verification: Zero Trust emphasizes strong device authentication, ensuring that only known and trusted devices can access sensitive resources. This approach mitigates the risks associated with compromised or untrusted devices.
Real-Time Sentinel: Real-time monitoring and analytics form a crucial pillar of Zero Trust. It enables organizations to detect anomalies, detect potential threats, and respond rapidly to any security incidents. Also, automated processes detect and respond to threats in real-time, reducing manual intervention and improving response times.
Agile Security Measures: Zero Trust incorporates adaptive controls to dynamically adjust the security posture based on contextual factors, such as user location, behavior, and device profile. It allows organizations to provide a frictionless user experience while maintaining a robust security posture.
Enhanced Security with Zero trust framework:
The introduction of the Zero Trust Framework addresses several critical issues:
Internal Threats: Internal threats pose a considerable risk because they can exploit insider privileges or compromised credentials to gain unauthorized access. The Zero Trust approach acknowledges the possibility of attackers already within the network and focuses on continuous verification of all entities, whether they are users, devices, or applications. This means that even if someone gains initial access, they are subject to ongoing scrutiny to ensure their activities remain legitimate.
Lateral Movement: Conventional security models often focus on fortifying the network perimeter, but they often fail to prevent threats from moving laterally within the network after an initial breach. Zero Trust addresses this concern by implementing network isolation 2.0(micro-segmentation) to restrict the movement of threats within the network, limiting potential damage. In essence, even if an attacker infiltrates one segment, they won't have free rein to roam throughout the network.
Perimeterless Operations: The emergence of cloud computing and remote work has rendered the traditional network perimeter less effective. In a world where assets can be spread across various cloud environments and accessed remotely, the Zero Trust Framework offers a superior way to secure these assets regardless of their physical or virtual location. This approach assumes that no location, device, or user can be inherently trusted, and thus enforces strict identity verification and access controls irrespective of where the asset is situated.
Attack Surface Reduction: Zero Trust tackles the issue of implicit trust that can widen the attack surface. In traditional models, users and systems often receive broad access privileges based on their roles, creating potential vulnerabilities. The Zero Trust approach emphasizes the principle of least privilege, ensuring that access is granted only when explicitly needed and authorized. This granular approach significantly reduces the attack surface by limiting the potential points of entry for attackers.
Data Protection: This includes implementing robust encryption mechanisms to secure data both at rest and in transit. Additionally, Zero Trust enforces controlled access to data, ensuring that only authorized users and applications can interact with sensitive information. By combining encryption and access controls, Zero Trust helps mitigate the risk of data breaches and unauthorized data exposure.
Zero Trust for Remote Work:
As the concept of remote work continues to gain traction in the modern workplace, it has become imperative for organizations to prioritize the security of their remote workforce. Endpoints, such as laptops and mobile devices, are often the entry points for security breaches in remote work scenarios. With the shift to remote work, traditional VPN solutions may not suffice in meeting security requirements. To address the unique challenges posed by remote work, the implementation of a Zero Trust framework emerges as a game-changer – a holistic approach that considers every user and device potentially untrusted, regardless of their location.
Zero Trust network access (ZTNA) solutions provide an enhanced alternative, offering granular and context-aware access to applications and resources. By dynamically verifying user identities and device posture, ZTNA solutions establish secure connections without granting unnecessary network access.
Remote workers often prioritize ease of access and productivity. Achieving a balance between user experience and security is crucial. Implement adaptive access controls that dynamically adjust based on user context, such as location and device. Leverage single sign-on (SSO) and passwordless authentication methods to simplify user login processes. Deploy user-friendly mobile security applications that protect against threats while ensuring an optimal user experience.
Embracing Zero Trust:
As our reliance on digital infrastructure grows, investing in a Zero Trust framework is essential for securing our valuable assets and ensuring the integrity of our systems. By implementing a Zero Trust architecture, we can minimize the risk of breaches, protect critical data, and fortify our security defenses against evolving threats. It brings about a fundamental shift in security philosophy. It involves rethinking traditional network architectures, embracing modern identity and access management tools, and fostering a security-first mindset across the organization. Remember, security is not a destination but a continuous effort.
If you find this post enjoyable, kindly consider subscribing and sharing it with your friends. I dedicate my free time to this, and witnessing the readership expand encourages me to stay motivated and keep writing. Many thanks!